Achieve measurable outcomes with expert-led Technology Adoption
Quickstart Your IT
Transformation
Transformation
How Technology Adoption Works
Empowering Teams with Powerful Tools and Expertise for Faster Results
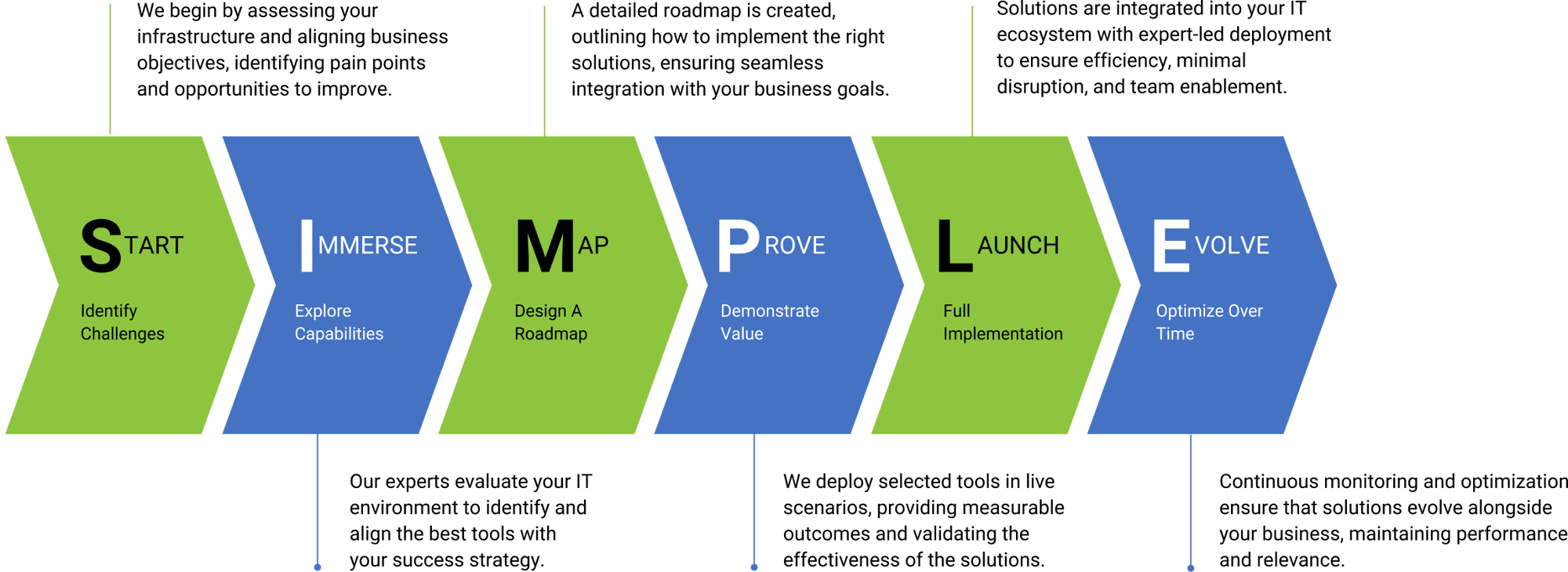
Explore Some Tailored Adoption Strategies
Technology Adoption Across Core IT Pillars
Data Center and AI Networking Solutions
Modern data centers and AI-driven networks demand flexible, high-performance solutions. Cisco’s portfolio, combined with BTA’s expertise, ensures seamless connectivity, simplified management, and optimized scalability for your IT infrastructure.
- Cisco Hyperfabric: High-speed, low-latency fabric architecture for modern data centers.
- Cisco ACI (Application Centric Infrastructure): Streamline data center operations with policy-driven automation.
- Cisco Nexus Dashboard and NX-OS: Centralized management for network optimization and performance monitoring.
- Cisco AIPod: AI-powered networking solutions to enhance scalability and automation.
Security Solutions: Breach Protection
In an era of escalating cyber threats, Breach Protection safeguards critical systems by identifying and neutralizing threats like malware, ransomware, and phishing attacks. These tools deliver rapid detection and response to prevent security incidents before they escalate.
- Cisco XDR Essentials: Monitor and respond to threats across your IT environment.
- Cisco Email Threat Defense: Block phishing and advanced email attacks.
- Cisco Secure Endpoint Advantage: Safeguard endpoints with advanced threat detection and response.
Security Solutions: User Protection
With workforce mobility and remote access becoming the norm, User Protection ensures that only authorized users gain access to critical systems. These solutions strengthen identity management and access control while maintaining user convenience.
- Cisco Secure Access: Enable secure access to apps and data from any location.
- Cisco Duo: Multi-factor authentication to verify user identities.
- Cisco Identity Services Engine (ISE): Centralize and automate identity management for secure user access.
Security Solutions: Cloud Protection
Cloud workloads introduce unique security challenges. Cloud Protection tools monitor traffic, enforce segmentation, and maintain compliance across distributed environments to ensure your multi-cloud infrastructure remains secure.
- Cisco Multicloud Defense: Protect data and applications across multi-cloud environments.
Secure Workload SaaS: Gain visibility and control over workload communications.
Vulnerability Management: Identify and mitigate risks in cloud environments. - Cloud Application Security: Monitor and secure cloud-hosted applications.
- Attack Surface Management: Discover and manage exposed cloud assets.
Detection Solutions: Real-Time Threat Detection
Cisco’s advanced monitoring tools and analytics provide real-time insights to uncover vulnerabilities and manage risks before they escalate.
- Cisco ThousandEyes: Gain visibility into latency, packet loss, and disruptions across networks.
- Cisco Secure Workload: Analyze workload communications for proactive threat detection.
- Cisco Secure Application: Identify weaknesses and address them to safeguard your environment.
Optimization Solutions: Achieve Operational Efficiency
Optimize workflows, ensure seamless integration, and improve performance across hybrid environments.
- Cisco Secure Application: Automate checks and streamline audit preparation.
- Cisco ISE: Ensure regulatory alignment through automated policy updates.
- Cisco Multicloud Defense: Address risks to maintain operational integrity.
Observability Solutions: Proactively Manage Compliance and Risk
Centralized dashboards and real-time monitoring ensure operational excellence while meeting regulatory standards.
- Compliance Monitoring via Cisco Secure Application: Automate checks and streamline audit preparation.
- Policy Governance with Cisco ISE: Ensure regulatory alignment through automated policy updates.
- Risk Mitigation with Cisco Multicloud Defense: Address risks to maintain operational integrity.
.png?width=220&height=79&name=BTA%20Color%20Black%201%20(1).png)