Detect threats in real-time to safeguard critical assets and mitigate risk
Our Detect services leverage AI/ML-driven solutions and cutting-edge tools like Extended Detection and Response (XDR) to provide 24/7 visibility, proactive threat detection, and rapid response capabilities—all tailored to your unique IT environment.
Proactive Detection Services for a Secure IT Ecosystem
Our Detect services combine state-of-the-art monitoring tools and threat intelligence to help you identify, assess, and neutralize risks in real time. From vulnerability detection to response automation, we ensure your IT operations remain secure and resilient.
Extended Detection and Response (XDR)
Gain full threat visibility across your IT infrastructure with XDR. By aggregating and analyzing data from endpoints, networks, and servers, XDR enables real-time detection and response to sophisticated threats, minimizing disruptions and ensuring faster, more effective threat management.
- Threat Correlation: Combines data from multiple sources to identify patterns and potential breaches.
- Automated Response: Neutralizes threats automatically, reducing downtime and impact.
- Behavioral Analytics: Detects anomalies to uncover threats before they materialize.


Firewall Change and Event Management
Ensure security integrity with advanced tools that monitor and manage firewall changes and events to prevent vulnerabilities. This approach enhances firewall reliability, reduces risk exposure, and streamlines change management processes.
- Event Monitoring: Tracks all firewall events in real time for instant threat identification.
- Change Management: Ensures all firewall updates are secure, compliant, and properly documented.
- Risk Analysis: Highlights the potential impact of changes on your network’s security posture.
Penetration Testing and Vulnerability Assessments
Proactively uncover weaknesses in your IT infrastructure with comprehensive testing and analysis. Strengthen defenses by addressing vulnerabilities before they can be exploited.
- Simulated Attacks: Uncover exploitable vulnerabilities before malicious actors do.
- Detailed Reporting: Provides actionable recommendations to address security gaps.
- Ongoing Assessments: Ensures your environment evolves with emerging threats.

I would say that BTA has knocked it our of the park that the team we're working with as part of the engagement has been fantastic. They’ve been able to really take it by the horns and not only get it implemented but allow us to learn as they're implementing.
- Steve Kitzinger, Director to IT Operations at CGB
Our Approach to Simplifying Threat Detection
At BTA, we leverage our S.I.M.P.L.E. methodology—Start, Immerse, Map, Prove, Launch, Evolve—to deliver advanced threat detection and response. By integrating AI-driven insights, automated monitoring, and real-time analytics, we help you identify vulnerabilities, address risks proactively, and ensure a secure IT environment.
Consulting & Advisory
Analyze your security infrastructure and threat detection capabilities to identify gaps, enhance monitoring, and align strategies with your risk management objectives.
Managed Services
Monitor your environment continuously to detect and respond to threats, ensuring critical applications and intellectual property remain secure while minimizing downtime.
Deployment
Implement advanced threat detection systems with precision. Automate monitoring and configure real-time response mechanisms to protect your infrastructure against evolving risks.
Optimization
Refine your detection capabilities with ongoing analysis. Optimize monitoring tools, policies, and workflows to improve visibility and ensure proactive threat management.
Enablement
Leverage our Quickstart Programs to deploy cutting-edge detection technologies tailored to your goals. Our S.I.M.P.L.E. methodology ensures efficient and effective implementation.
Mentoring
Empower your teams with the skills and knowledge needed to operate and maintain advanced threat detection systems. Our mentoring programs ensure sustainable success and operational excellence.
Why Choose BTA for Detection?
Proactively identifying and responding to threats requires expertise, technology, and a results-driven approach. With 1,000+ completed projects and decades of experience, we simplify threat detection and strengthen your security posture so you can focus on your goals.
55%
80%
75%
Cutting-Edge Tools: Architect Explorer™ delivers actionable insights, real-time risk detection, and automated policy enforcement to enhance security and streamline operations.
Proven Expertise: Our team has extensive experience in threat detection, compliance, and automated response strategies, ensuring secure, responsive, and scalable solutions.
S.I.M.P.L.E. Framework: Our streamlined and efficient approach (Streamlined, Innovative, Measurable, Practical, Leveraged, Efficient) accelerates threat detection and delivers actionable results.
Tailored Guidance: We align detection strategies with your business goals, offering expert advisory and customized training to empower your team and ensure lasting success.
How Architect Explorer™ Helps You Detect Vulnerabilities
Architect Explorer™ delivers the intelligence and automation needed for proactive threat detection and response. By providing real-time insights and streamlining security operations, it ensures faster risk identification and resolution.
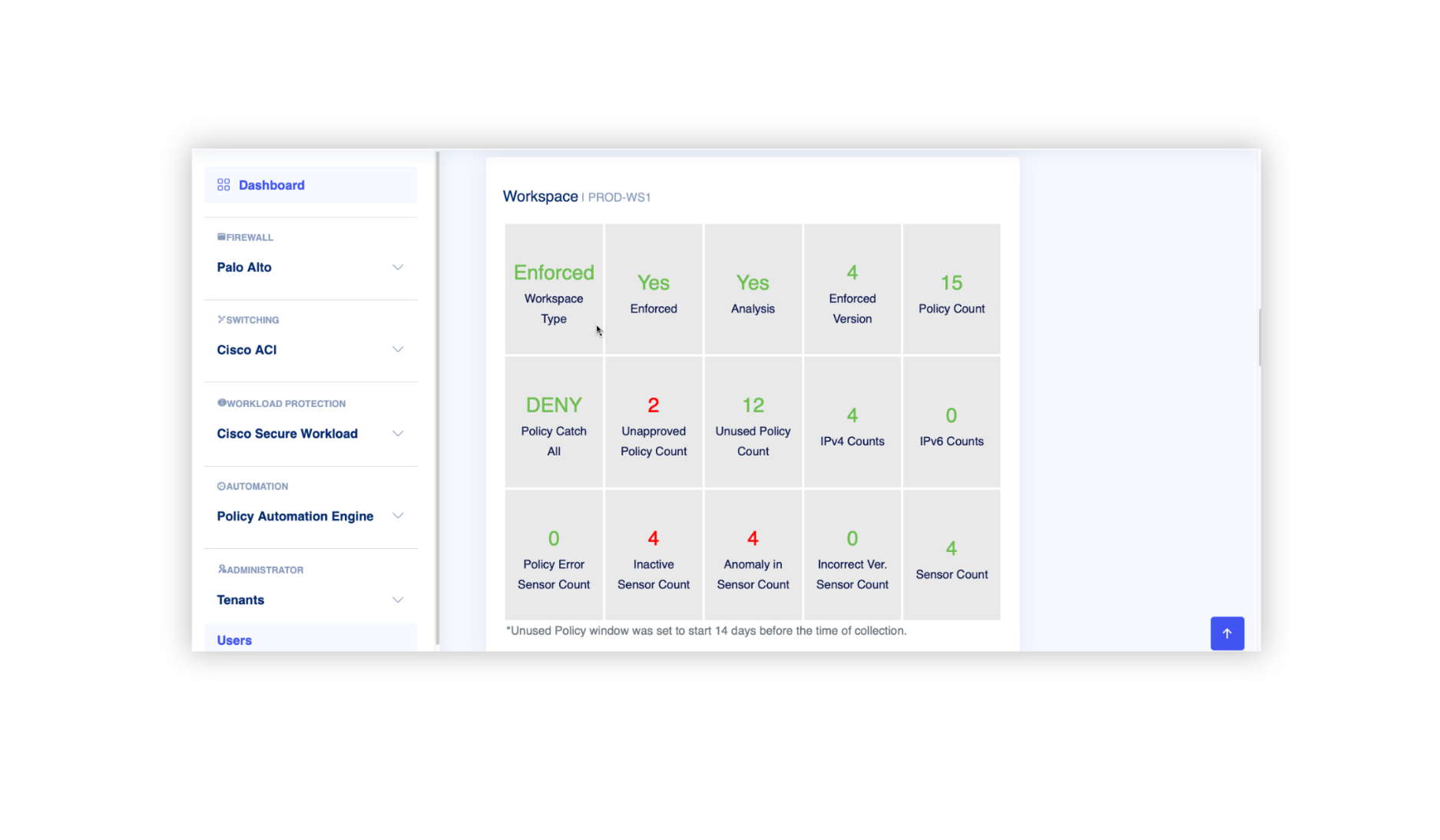
Key features
- Real-Time Threat Visibility: Comprehensive dashboards for tracking potential risks.
- AI Powered Risk Prioritization: Highlights critical threats for immediate action.
- Unified Monitoring: Consolidates data from multiple sources for holistic threat detection.
Translated Benefits
- Faster Incident Response: Respond to risks with actionable insights in real time.
- Threat Impact Minimization: Reduce potential damage through early detection and response automation.
- Enhanced Team Efficiency: Free up your IT team to focus on strategic initiatives by automating threat management tasks.
Don’t Take Our Word For It. See What Our Clients Say
Operations for Businesses Like Yours.
.png)
CASE STUDY
Enhancing Visibility and Segmentation to Mitigate Risk
Discover how BTA leveraged Cisco ACI and Secure Workload to help a Global Construction Company achieve visibility, enforce microsegmentation, and secure critical workloads for compliance and risk management.
Cisco Partnership Advantage
Cisco solutions like XDR provide seamless integration, real-time monitoring, and optimized performance for proactive threat management.
.png?width=225&height=90&name=Logos%20BTA%20(500%20x%20200%20px).png)