Unlock the Full Potential of Your IT Infrastructure
Architect Explorer™: Transforming IT Operations with Advanced Automation and Insights
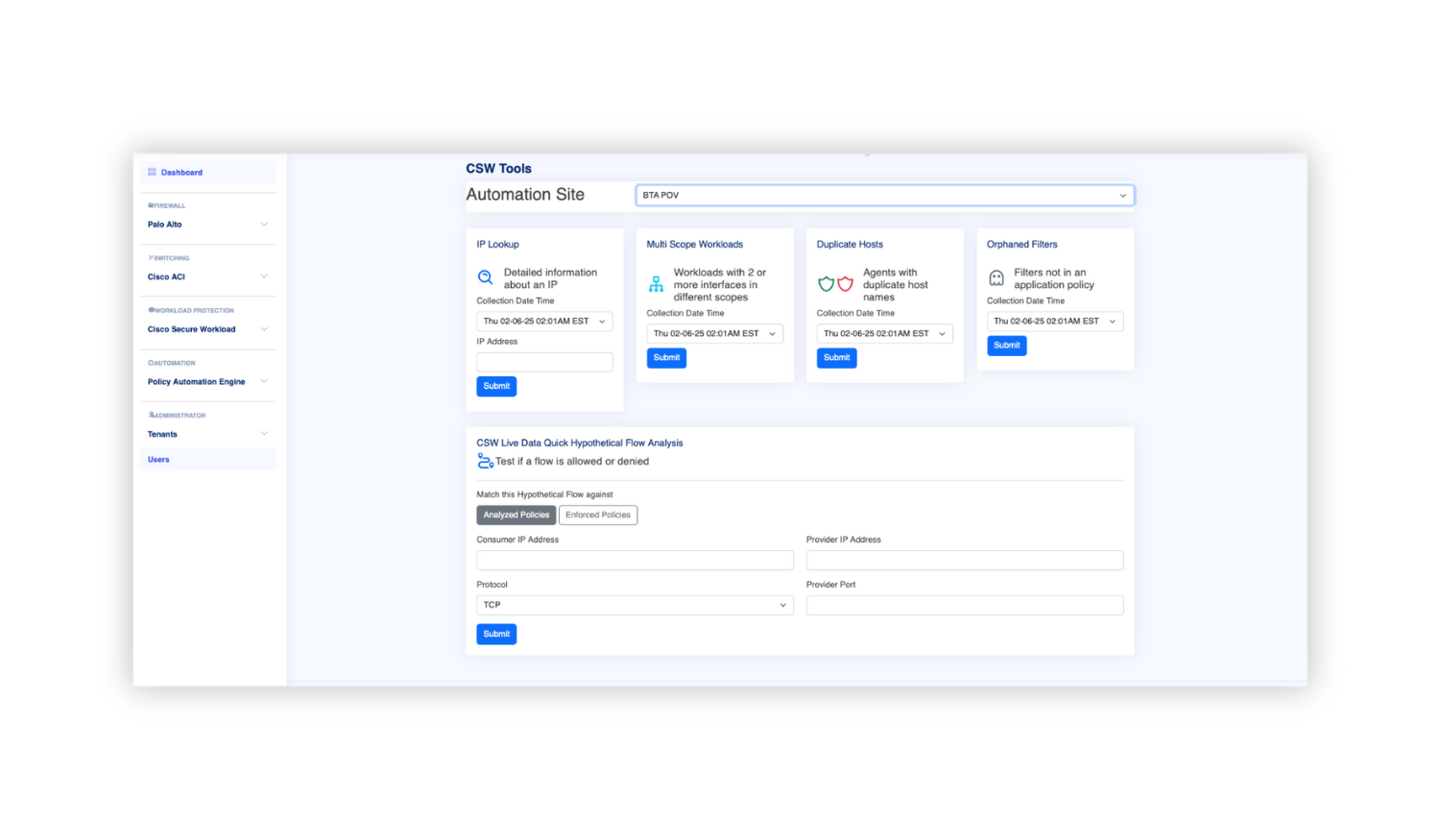
How Architect Explorer™ Drives Business Success
Streamlined Policy Visualization
Architect Explorer™ converts complex configurations into clear, actionable visuals, helping IT teams quickly identify inefficiencies and reduce policy conflicts.
Automated Policy Lifecycle Management
Enhance efficiency by automating the creation, testing, enforcement, and retirement of policies. Save time and resources while ensuring consistent enforcement across hybrid IT environments.
Conflict Detection and Resolution
Maintain operational harmony by automatically identifying and resolving policy conflicts, reducing risks associated with misconfigurations.
Comprehensive Compliance Reporting
Simplify regulatory compliance with pre-built templates and detailed audit reports. Architect Explorer™ ensures your environment aligns with standards like HIPAA, PCI DSS, and GDPR.
Real-Time Monitoring and Alerts
Proactively address issues with real-time alerts and actionable insights. Optimize performance, detect anomalies, and maintain a secure IT ecosystem.
Integration-Ready for Ecosystem Expansion
Architect Explorer™ integrates seamlessly with existing IT tools and platforms through APIs, ensuring flexibility and scalability as your business evolves.
Saves a LOT of time for engineers to compile & compare policies for approvals. We should’ve started with this.
- Anonymous
How to Implement
Architect Explorer™
Architect Explorer™
Simplify Adoption with Proven Strategies
Cisco Partnership Advantage
.png?width=130&height=130&name=27%20(1).png)
.png?width=130&height=130&name=27%20(2).png)

.png?width=130&height=130&name=27%20(3).png)
.png?width=130&height=130&name=27%20(4).png)


%202.png?width=130&height=130&name=Logos%20BTA%20(4)%202.png)


Don’t Take Our Word For It. See What Our Clients Say

CASE STUDY
Securing IoT Devices with Architect Explorer™
Discover how a Global Mining Company leverage Architect Explorer™ to combine device intelligence and field-proven processes to enable quick & secure application segmentation, at multiple policy enforcement points.
FAQs
Architect Explorer™ is an IT operations platform that simplifies complex environments with automated policies, real-time insights, and advanced analytics to enhance security and compliance.
It streamlines policy creation, enables dynamic segmentation, and provides deep visibility into network and application behavior, helping teams reduce risk and make faster, smarter decisions.
Architect Explorer™ automates the full policy lifecycle—creation, testing, enforcement, and retirement—while detecting and resolving conflicts to ensure consistent enforcement across hybrid environments.
The platform offers pre-built compliance templates and detailed audit reports, helping organizations align with standards such as HIPAA, PCI DSS, and GDPR.
Yes. It provides real-time monitoring and alerts, enabling IT teams to detect anomalies, optimize performance, and proactively maintain a secure IT ecosystem.
Architect Explorer™ is integration-ready, connecting through APIs to existing IT tools and enhancing Cisco technologies to create a unified, automated approach to IT management.
BTA uses a structured, tailored implementation approach that simplifies adoption, aligns with business needs, and accelerates time-to-value through proven strategies and expert guidance.
.png?width=225&height=90&name=Logos%20BTA%20(500%20x%20200%20px).png)