CYBERSECURITY
Protect Your Network and Your Brand With Proven Cybersecurity Solutions Delivered by Professionals

Modernize Your Networks with Cybersecurity that Keeps Your Business Running
Strong cybersecurity is a moving target. Implementing robust and flexible solutions, tailored to defend against evolving digital threats, is something we take very seriously. Our team leverages more than 35 years of experience fortifying enterprises by implementing smart network systems.
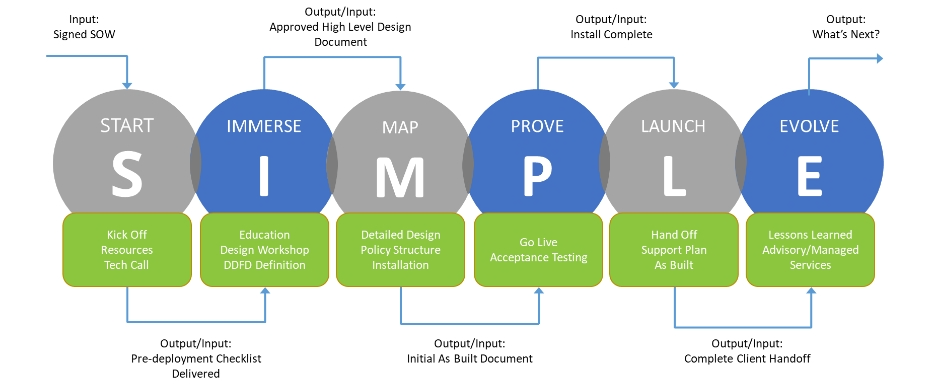
Our S.I.M.P.L.E. Approach Makes it Attainable. Cybersecurity doesn’t have to be painful. At BTA, we use our proven S.I.M.P.LE. methodology to provide the highest quality outcomes in a fraction of the time, so that your organization sees business value faster.
Cybersecurity helps an organization:
-
Safeguard the Organization from costly losses that occur from data breaches or other security incidents.
-
Ensure Legitimate Access to systems and applications that balance internal and external protection in a manner that maintains productivity across the enterprise.
-
Implement Next Generation Firewalls that allow you to consistently focus on blocking sophisticated malware and advanced application-layer attacks efficiently.
-
Align with Zero Trust Policies to ensure your organization is compliant and a trusted organization to work with.
Cybersecurity Solutions
Proper network security involves a combination of hardware, software, and process configurations that protect your network from data breaches, intrusions and other cyber threats. Regardless of the mix of systems that need to work together, our experienced team can help you create the best approach for your organization. To flexibly adapt to your complex network environment, our cybersecurity solution also includes:
Our Cybersecurity Solutions also Include:
Cisco Secure Workload
Maximize workload security with Cisco Secure Workload, the frontrunner in adaptive protection across multi-cloud environments. Seamlessly enforce zero-trust policies, bolster micro-segmentation, and shield your resources no matter where they reside. Let us empower your infrastructure with unmatched Cisco resilience and agility.
Identity Services
Engine
Harness the power of the Identity Services Engine to fortify access control across your digital realm. With precision management of identities and policies, ensure that only authorized entities gain access to your vital resources. Step into a world of enhanced security, streamlined compliance, and robust policy enforcement.
XDR
(Extended Detection and Response)
Elevate threat management with XDR, the pinnacle of proactive cybersecurity approaches. Offering a panoramic view across endpoints, XDR ensures swift detection and rapid remediation of potential threats. Embrace the next-gen in cybersecurity, ensuring holistic defense and agile response capabilities.
DUO
(Multi-Factor Authentication)
Boost your security layers with DUO, the leader in multi-factor authentication solutions. Add an invaluable layer of user verification, ensuring that every access is legitimate and safeguarded. With DUO, confidently mitigate risks, prevent unauthorized access, and enhance user trust.
CSW Microsegmentation
You’ll learn how to segment your applications fast, reliably, and securely with our CSW Microsegmentation Workshop. Our extensive experience with CSW has allowed us to identify a set of use cases that are universally applicable. We’ve built and fine-tuned these use cases so you can quickly see the advantages of application segmentation.
CSW Engagement Workshop
BTA’s CSW Engagement Workshop focuses on technological capabilities and business objectives, delivering real business benefits and technical competence. The Workshop follows a proven, structured process that involves identifying business processes and applications, examining the current IT environment, and helping you define a CSW implementation strategy.
Security Architecture Consulting Services
Our security experts work with customers around the world to assess existing security methodologies, recommend modernization techniques, and provide actionable paths forward. Our goal is to ensure enhanced security protection and agility combined with complete operational alignment.
Security Architecture Advisory Services
Determining the best solution involves evaluating current practices, developing a design, determining configuration, creating policy, and outlining automation requirements, as well as topology and fabric layout.
Security Architecture Managed Services
BTA will assist in the protection of intellectual property against ransomware, the segmentation of essential applications, and the rapid migration to new security architecture. Our management service team manages and maintains your environment, handles daily care and feeding, and monitoring. We'll cover routine changes and resolve any problems that arise.
Security Architecture Deployment Services
Whether you’re a small or medium-sized firm looking to safeguard sensitive customer data or a major corporation in search of assistance with your enterprise architecture, BTA is here to help. Our team’s diverse skillset enables us to take on everything from project management to mentorship and knowledge transfer.
Security Optimization Services
BTA is here to help you achieve scalable and manageable Zero Trust workload protection. At BTA, our expert practices and proven approach will provide deep insight into your infrastructure identity, where it may be lacking as it relates to your IaaC or microsegmentation workloads. We’ll make sure you get the most out of your security architecture by optimizing resources, prioritizing workloads, segmenting applications, reconfiguring policies, automating processes, and eliminating vulnerability gaps. Using our proven methodology, our team will design a solution that meets business and regulatory requirements.
Ask About our Recent Case Study on Enterprise Security Architecture Services
