Protect your critical data, apps and networks with Zero Trust and Compliance-Driven Solutions
Plus, with advanced tools like the Policy Automation Engine (PAE) and AI/ML-driven Architect Explorer™, we reduce security breaches, accelerate incident resolution, streamline compliance, and optimize network operations.
Strengthen Your Security Posture with Tailored Protect Solutions
Our Protect services combine robust frameworks with advanced automation and networking solutions to secure your environment, fortify defenses, and deliver measurable results.
Zero Trust Frameworks
We deliver a customized Zero Trust architecture that enhances your security posture by limiting unauthorized access and adapting to evolving threats. Our approach secures critical systems, minimizes risks, and ensures regulatory compliance.
- Identity Access Control: Role-based access tied to user behavior and device attributes.
- Micro-Segmentation: Divides networks into smaller, secure zones to contain threats and limit lateral movement.
- Dynamic Enforcement: Adapts policies in real-time to address evolving threat landscapes.
.jpg)

Policy Automation Engine (PAE)
Our PAE enhances operational efficiency by automating policy management across hybrid and multi-vendor environments. This solution helps streamline workflows, prioritize high-risk issues, and ensures compliance with industry standards, saving time and reducing manual effort.
- Automated Policy Creation: Consistently generate and enforce policies across all environments.
- AI-Powered Policy Ranking: Quickly identify and prioritize critical risks for faster resolution.
- Automated Compliance Monitoring: Maintain alignment with HIPAA, PCI DSS, and other regulatory requirements.
Firewall And Cloud Protection
We combine firewall services with advanced cloud protection to secure on-premises and cloud environments, ensuring defense, optimized performance, and continuous monitoring for peak network health.
- Advanced Auditing: Identify misconfigurations, unused rules, and vulnerabilities.
- Rule Set Optimization: Streamline firewall rules for better security and performance.
- Cloud Security: Utilize XDRaaS for detection and Port53 for DNS-layer protection.
- Micro-Segmentation Support: Align policies to contain threats and safeguard sensitive areas.
- Continuous Monitoring: Maintain network health with ongoing checks.


Compliance Alignment
We simplify compliance management by embedding regulatory requirements into your policies and processes. Through automated workflows and centralized reporting, we help you stay audit-ready while reducing compliance-related costs and risks.
- Real-Time Compliance Monitoring: Continuous checks to ensure adherence to standards like CMMC and GDPR.
- Industry-Specific Frameworks: Tailored compliance solutions for healthcare, finance, manufacturing, and more.
- Centralized Reporting: Streamlined audit preparation with transparent and accessible compliance insights.
It’s absolutely critical that you use a business partner that is tried, true, dedicated, and brings forward expertise in the field, and that’s exactly what BTA did for us.
- Pam Austin, CIO at Ballad Health
How We Protect Your Business
We tackle security challenges with tailored solutions and the right delivery model. From advisory services to hands-on implementation and proof-of-value engagements, our offerings cover every aspect of business protection. Guided by our S.I.M.P.L.E. methodology, we ensure streamlined processes and proven results.
Consulting & Advisory
Assess security strategies and network infrastructures, identify modernization opportunities, and develop actionable plans for enhanced protection and operational alignment.
Managed Services
Protect intellectual property, segment critical applications, and maintain secure environments with daily monitoring, proactive issue resolution, and optimized network performance.
Deployment
Implement secure architectures, automate processes, and safeguard critical assets with expert-led project management and mentorship tailored to your unique needs.
Optimization
Assess security strategies and network infrastructures, identify modernization opportunities, and develop actionable plans for enhanced protection and operational alignment.
Enablement
Through our Quickstart Programs, we use the S.I.M.P.L.E. methodology and cutting-edge technologies to identify and implement the precise solutions your business needs to achieve its goals quickly.
Mentoring
Our mentoring programs combine real-world expertise and practical training to drive long-term success. Empower your teams to adopt ad sustain new technologies.
How Architect Explorer™ Helps You Protect Your Business
Our holistic approach, combining core capabilities in security, networking, and automation along with specialized services and flexible delivery models, ensures businesses can protect assets, detect threats, optimize IT operations, and observe their environments for continuous improvement.
55%
80%
75%
Cutting-Edge Tools: Leverage core capabilities like Zero Trust frameworks, network optimization, and automation to streamline operations and secure critical assets.
Proven Expertise: Our team brings deep knowledge in Zero Trust frameworks, compliance, automation, and network optimization, ensuring secure and scalable IT systems.
S.I.M.P.L.E. Framework: Our structured approach (Streamlined, Innovative, Measurable, Practical, Leveraged, Efficient) transforms IT challenges into growth opportunities.
Tailored Guidance: We align security strategies with your business goals, offering expert advisory and customized training to empower your team and ensure lasting success.
How Architect Explorer™ Helps You Protect Your Business
Architect Explorer™ serves as the foundation of the Protect pillar, providing actionable insights to streamline operations and enhance both networking and automation. It empowers IT leaders to address vulnerabilities, uphold compliance, and make confident, data-driven security decisions.
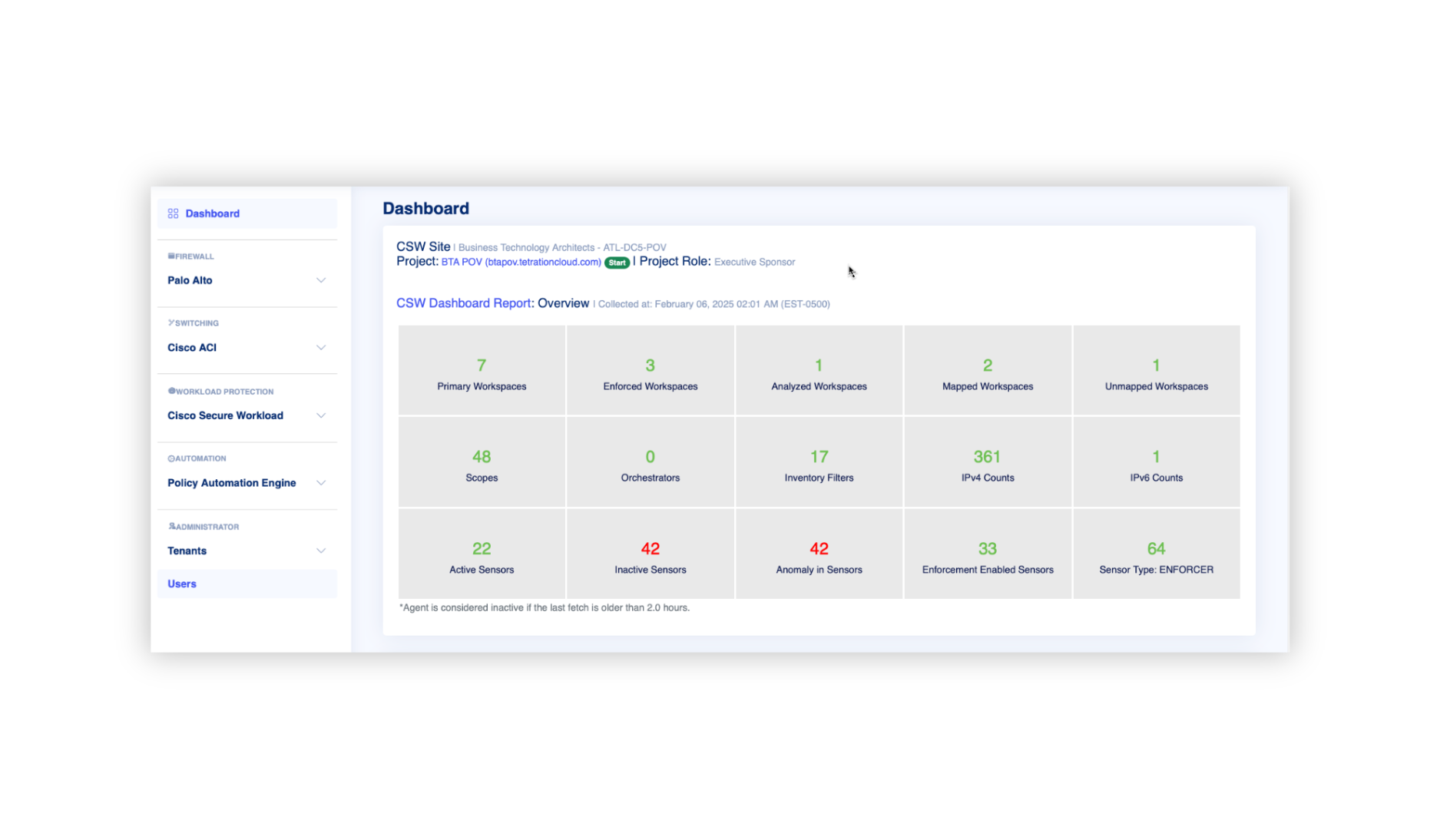
Key features
- Real-Time Auditing: Automated updates to identify and address risks promptly.
- Customizable Dashboards: Tailored analytics for monitoring security and compliance.
- Integrated Insights: Unified visibility into your security environment to proactively manage risks.
Translated Benefits
- Faster Auditing: Reduce policy review times by up to 55%, enabling quicker response to business needs.
- Policy Validation and Rollback: Ensure secure and reversible changes to maintain system stability.
- Custom Reporting: Provide detailed insights to enhance compliance and risk management.
Don’t Take Our Word For It. See What Our Clients Say
Operations for Businesses Like Yours.
.png)
CASE STUDY
Securing IoT Devices with BTA’s Policy Automation Engine (PAE)
Discover how a Global Mining Company leverage BTA’s Policy Automation Engine (PAE) to combine device intelligence and field-proven processes to enable quick & secure application segmentation, at multiple policy enforcement points.
Cisco Partnership Advantage
From seamless integration to optimized infrastructure performance, Cisco solutions like Secure Firewall and ISE ensure robust protection, compliance, and threat prevention for your critical assets.
.png?width=225&height=90&name=Logos%20BTA%20(500%20x%20200%20px).png)